 Used to disguise malicious file extensions, this legacy functionality is being repurposed in attacks to obfuscate attachment types and steal credentials in an impressive way.
Used to disguise malicious file extensions, this legacy functionality is being repurposed in attacks to obfuscate attachment types and steal credentials in an impressive way.
Some languages in the world (such as Hebrew and Arabic) read right-to-left, as opposed to most languages (including English) that read left-to-right. To account for this, years ago, a non-printing Unicode character was devised [U+202e] to create a “right-to-left override”, better known as RLO.
For example, if I was to use that Unicode character in the phrase “Cyber[U+202e]Security”, it would be displayed “CyberytiruceS”. Now, apply this concept to, say, a malicious filename: “MaliciousAttachment[U+202e]pdf.exe” would be displayed in Windows as “MaliciousAttachmentexe.pdf”. You can quickly see how this can take a file that is obviously suspicious at least, and make it appear very much benign, and even seem business-appropriate.
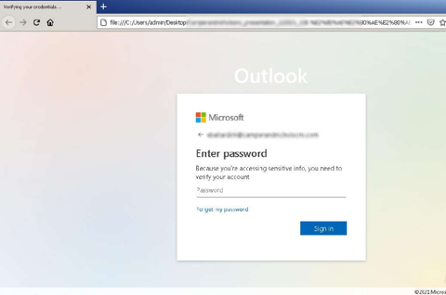
In a new attack documented by security vendor Vade Secure, this method of obfuscation and social engineering has been seen recently in the wild targeting Microsoft 365 users. In the attack, victims are sent an email with a “voice mail” attached with a filename that ends in “mth.mp3”. Now, remember the RLO principles and you realize with the right placement of the Unicode character, this becomes “mp3.htm” – an HTML file! The HTML is loaded in the browser and the user is presented with a Microsoft 365 logon screen:
Source: Vade Secure
Behind the scenes, the HTML code includes a POST command to a server controlled by the attackers that will eventually contain the credentials entered by the victim user.
The big red flag here is receiving a voicemail in your inbox as an attachment. Users that undergo Security Awareness Training will spot this immediately and – at very least – find it suspicious. Proper training tells them to not engage with such content, helping to avoid becoming a victim of these attacks.
 Here's how it works:
Here's how it works:




